Secret Names
Secret names are limited to 64 characters in length, must be alphanumeric (with underscores) and are automatically uppercased. 📝 Secret name regex, for your convenience:^[a-zA-Z0-9_]{1,64}$
Managing Secrets
- CLI
- Console
Using Secrets
In Hop Deployments
When creating a deployment or individual container, you can set environment variables that point to project secrets. Their values will automatically be updated when you update the secrets. Every field where you’d usually put an environment value is compatible with secrets - you can just use${SECRETS.NAME} (where NAME is the secret key
name) and Hop will automatically replace it with the value when a container
starts.
Usage with hop deploy
When using hop deploy, you can specify environment variables with -e or
--env, so: for example, if I wanted to reference a project secret named
REDIS_URI in my deployment, I’d execute the following command:
Usage with Console
When creating a deployment, or when using the Environment tab in your deployment, you can set environment variable values to secret keys: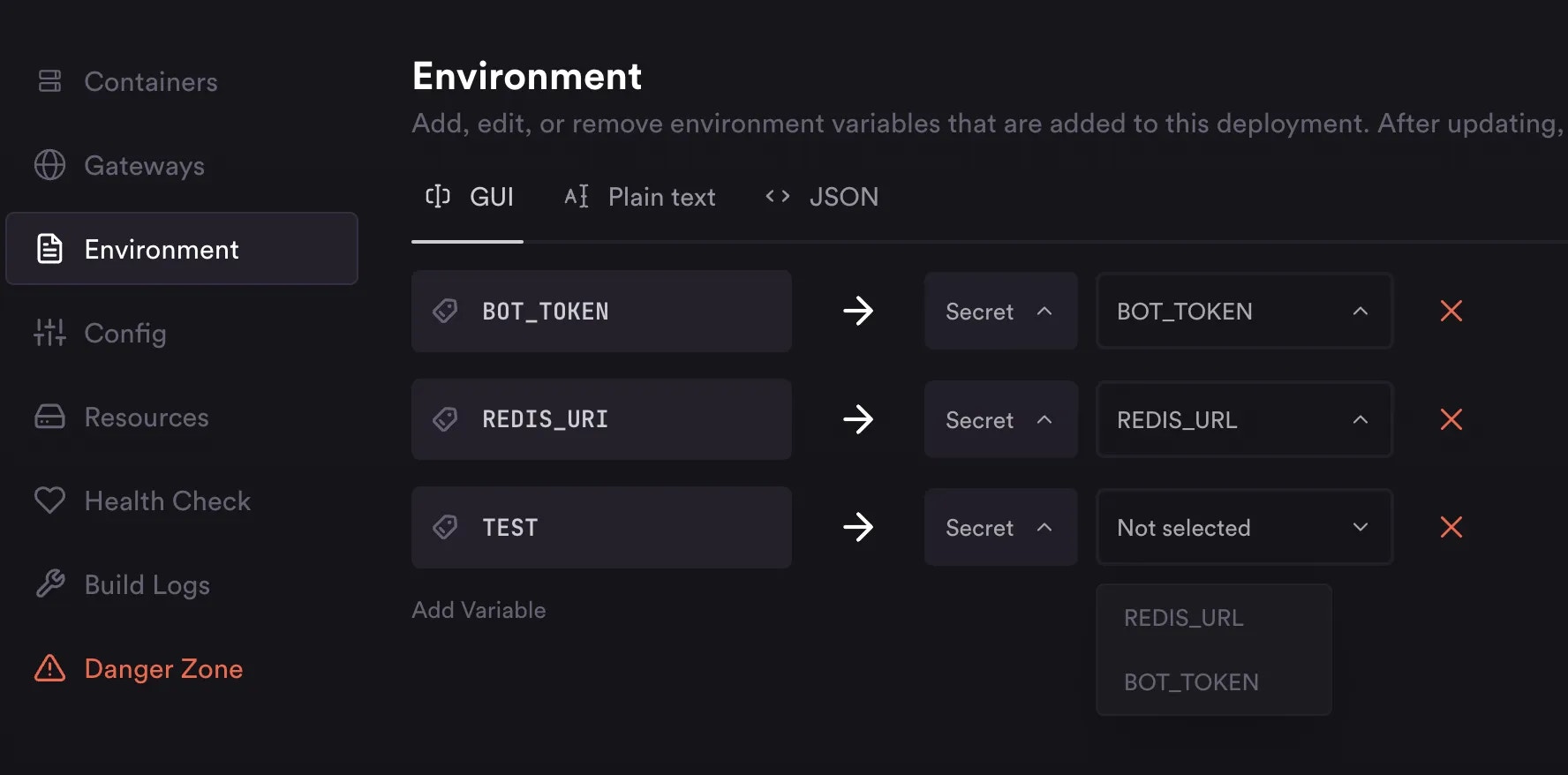
Usage with API
When setting environment variable values on API requests, you can just refer to secrets like you would with the CLI:${SECRETS.NAME}